Introduction
Do you know the main purpose of development of the internet? The Internet was developed so that computers could communicate with each other easily. Why do computers need to communicate with each other? The reason can be either to share data or resources. So, the computers share some information whenever they share data or resources. Most of the time, this information is private information that should not be visible or accessible to any other device. Thus, security is a very important aspect of computer networking.
The OSI Security model provides a standard architecture of security of the data for an organization. It is important to provide a well-defined and well-organized structure for the security so that the organizations can decide upon the security measure in a planned manner and the chances of data breaching or any such security threats are minimized.
So, let us study the OSI Security Architecture in detail.
What is OSI Security?
Before we understand what OSI Security is, let us first recall the OSI Model. Have a look at the image shown below:

OSI Model
The OSI model is a standard model for computer networking. This model provides the standards for communication between the devices by dividing the entire process of communication into a 7-layer model and different protocols being used in the different layers.
Confused about your next job?
However, we do not implement the OSI model practically. The TCP/IP model is the practically implemented model. Yet, the OSI model still plays a major role by providing standardization for protocols.
The data that starts from the Application layer of the sender, goes to the layers below and at each layer, a header is added to the data that might contain information like the sender’s address, receiver’s address, etc. When the data reaches the Physical layer of the sender, it has the headers of all the previous layers attached to it. Now, the data travels via a physical medium to the receiver and reaches the Physical layer of the receiver. The receiver then sends the data to the upper layers and each layer processes its header and removes it from the data so that when the data reaches the Application Layer of the receiver, it is in its original form.
OSI Security Model
So, we understood that the data travels from the Application layer of the sender to its Physical layer and then from the Physical Layer of the sender to the Physical layer of the receiver. So, in between, this data can be modified, stolen, or just being read by an attacker for some future use. This is not safe as the data can be used for criminal activities as well and in any big organization, the data being stolen/modified can be of major concern.
So, the OSI Security model provides a standard for the security of data by identifying the attacks, security services, and security mechanisms and also identifies which security services should be implemented in which layer of the OSI model and what security mechanisms should be used to do so. So, let us now understand the OSI Security Architecture model in detail.
OSI Security Architecture
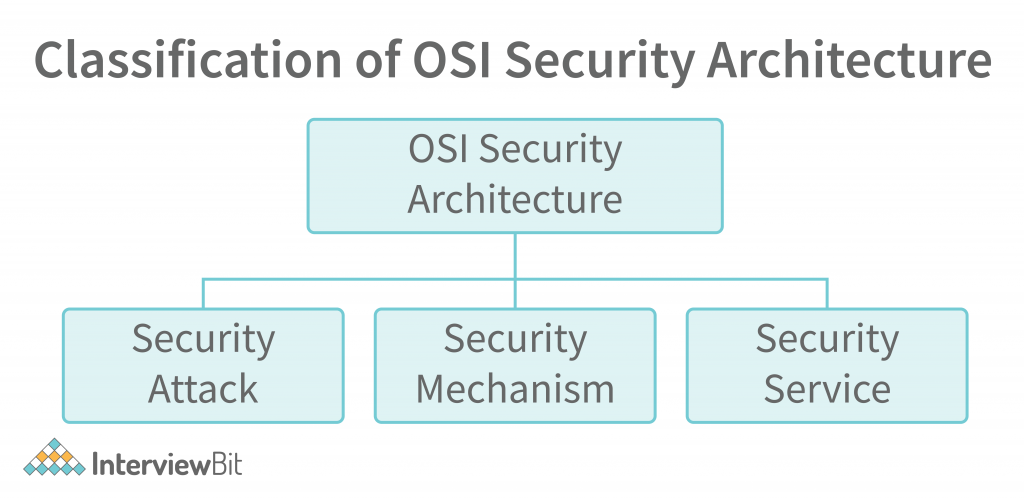
So, as we discussed, the OSI Security model identifies the attacks on a system (data) and also identifies various security services and the mechanisms to implement those services in various layers of the OSI model. Let us first discuss Security Attacks.
Security Attacks
A security attack means any action that puts the data or overall security of the system at risk. An attack might be successful or unsuccessful. In case of a successful attack, the attacker can complete his/her motive of breaking the security of the system in any way he/she wants to. In case of an unsuccessful attack, the system remains secured and no harm to the security is done. There are majorly 2 types of attacks: active attacks and passive attacks. Let’s discuss them in detail.
Passive Attack
A passive attack is a kind of attack in which the data that is sent from the sender to the receiver is read by the attacker in the middle of the transmission. However, the main point to note here is that the passive attack is the attack in which the attacker does not modify or corrupt the data. No changes are made to the data. The attacker just observes the data sent to the receiver from the sender and can know a lot of information about the sender and the receiver just by observing the communication between them. There are 2 types of passive attacks.
- Traffic Analysis: As the name suggests, this attack focuses on the amount or volume of data sent between the sender and the reciever.1. The attacker can predict a lot of information about the sender and the receiver by knowing the amount of data sent. For example, if a lot of data is being sent from the sender to the receiver, it is assumed as there is an emergency, or a task is happening on an urgent basis. If less data is shared between the sender and the receiver, it is assumed that there is a lack of communication and so on.
- Eavesdropping: In this kind of attack, the attacker reads the communication that happens between the sender and the receiver and then can use this information for many things. For instance, an attacker can use the information to know about the financial details of the user. Also, this can be used for criminal activities as the attacker can send a lot of personal information to a criminal. The difference between eavesdropping and traffic analysis is that in traffic analysis, the attacker does not even read the data. He/she is just focused on the volume of the data. Whereas on the other hand, in eavesdropping, the focus is on the actual data being exchanged between the sender and the receiver.
Active Attack
In an active attack, the focus of the attacker is to modify the data that is being exchanged between the sender and the receiver. The most dangerous thing about this attack is that most of the time, the sender and the receiver do not even know that an attack has happened. There are several types of active attacks. Some of them are as follows:
- Replay: In a replay attack, the attacker acts as an authorized user and can use the details of the authorized user to log in to a system. This happens as follows. Suppose that there is a user, and he/she wants to log in to a system. So, they enter their username and password, and this detail reaches in the form of a data packet to the server of the system. The attacker can steal this data packet in between and use this data packet later to log in to the system. You might be wondering that the login details are encrypted, so how would the attacker use them? The encryption will not matter in this case as the data packet as it is, has been stolen and the server might not recognize this and give access to the attacker.
- Masquerade: In this attack too, the attacker acts to be an authorized user. Now, this is not done by stealing the data packet. It is done by stealing the login details of the user somehow. So, no technical aspect of stealing the details is involved here.
- Denial of Service (DOS): The denial-of-service attack is an attack in which a system is attacked by a lot of requests to the system at one time that it is not able to handle. The attacker sends multiple requests to the server at the same time and the server is not able to handle such requests. However, this attack is easily identifiable as these loads of requests come from a single sender (the attacker) and it is easy to identify the source of the attack.
- Distributed Denial of Service (DDOS): As we saw, in the denial-of-service attack, the source of the attack can be easily identified. Now, there is a modified version of this attack i.e., DDOS i.e., distributed version of the DOS attack. In this attack, the attacker first observes the details of a lot of authorized users. Then, the attacker uses these authorized users at the same time to send requests to the system. Now, thousands (or even more) of requests at the same are sent to the system and the system cannot recognize the source of attack as there is each request from a different user, and all the users are authorized. So, the attacker is using the authorized users as victims too. The primary victim is the system, and the secondary victims are the authorized users. The authorized users are called Zombie PCs.
So, the OSI security model is also used to identify the types of attacks. Now, let us understand the second pillar of OSI security architecture i.e., Security services.
Security Services
These are the services that are used for maintaining security. These security services can be implemented in various layers of the OSI model. Security services can be divided into 5 major categories.
- Authentication: This is a very basic and easy service to implement. In authentication, the system (both sender and receiver) identifies the user first. Only the user authorized to enter the system can use it. This can be done using basic password protection.
- Access Control: In an organization, various levels of employees have various levels of access to the system. For example, in a company, a software engineer has limited access to the system as compared to the product manager and the product manager has limited access as compared to the CTO of the company.
- Confidentiality: This is one of the three pillars of the security model CIA (Confidentiality, Integrity, and Availability). Confidentiality means that the data i.e. is shared between a sender and receiver should be confidential to them only. No third party should be able to read the data.
- Integrity: This is the second pillar of the CIA. Here, integrity means that no third party should be able to modify the data i.e. is shared between the sender and the receiver.
- Non- repudiation: So, let us say that the sender sent some data to the receiver and the receiver has received the data as well. Now, the receiver refuses to accept that the data has been received. So, there should be a way to clarify and prove that the receiver has received the data. The same is the case otherwise. So, when there are means to identify this in the security model, it is called non-repudiation.
So, these were some of the major security services. Now, let us discuss the security mechanisms.
Security Mechanisms
The mechanisms that help in setting up the security services in different layers of the OSI model and that help in identifying any attack or data breach are called security mechanisms. The security mechanisms provide a way of preventing, protecting, and detecting attacks. Some of the security mechanisms are as follows
- Encipherment (Encryption): One of the most popular security mechanisms is encryption. The message/data sent from the sender to the receiver is usually encrypted to some format that even if the message is stolen, cannot be decrypted easily by the attacker. Some of the popular encryption algorithms are AES, RSA, Triple DES, etc.
- Traffic Padding: The sender and receiver send the data to each other. Now, sometimes there is a gap between the sender and receiver. This means that for some time when the sender and receiver are not sharing the data, the attacker can act as if it is the sender and send some data to the receiver to attack it. So, this can be avoided if the gap (empty time) between the sender and the receiver is not known to the attacker. For this, during the gap duration, the sender keeps on sending some dummy data to the receiver and the receiver knows that this is the dummy data by using some identification. Hence, no gap is created between the sender and the receiver and the attacker cannot attack the system.
- Routing Control: The messages that a sender sends to a receiver travel different routes, However, in some cases, the sender and receiver might communicate mostly via the same route. In this case, the attacker tracks this route and can make changes to the data or take advantage of this. So, routing should be controlled in such a way that mostly, a different route is selected between the sender and the receiver to deliver the message.
So, these were some of the security mechanisms that can be used to detect/prevent attacks. This is the complete OSI Security model. Let us now discuss some benefits of OSI Security Architecture.
Benefits of OSI Security Architecture
Some major benefits of the OSI Security Architecture are as follows:
OSI Security Architecture Provides Security
The security model is designed to provide security to organizations to prevent their data from being breached. Hence, the major goal is accomplished well by the OSI Security Architecture.
OSI Security Architecture Provides International Standards
It provides a worldwide standard for the security of systems. This standard can be followed by every organization in the world and does not need to worry about the separate implementation for each organization as the model has been designed to cater to all kinds of needs related to security.
Easy for the Managers
The OSI security model makes it easy for the managers to build a security model for the organization based on strong security pillars and principles. The managers do not have to think much out of the box on their own and can simply implement the OSI model as per the security requirements of their organization.
So, these were some of the benefits of OSI security architecture.
Conclusion
We hope that you understood the complete concept of OSI Security Architecture, its benefits, and its 3 pillars viz, attacks, security mechanisms, and security services. We conclude that the OSI Security Architecture is a very helpful security architecture model and it sets International Standards for security. So, with this, we conclude the topic. See you again at InterviewBit.