Palo Alto Interview Questions
Introduction:
We currently live in a digital era in which the internet, computers, and other electronic devices, as well as software programs, play an important role in our daily lives. The banking system, hospitals, financial institutions, governments, and manufacturing enterprises all rely on Internet-connected gadgets to perform their operations. The unauthorised access or disclosure to some of their data, such as intellectual property, financial data, and personal information, could have serious consequences. Intruders and threat actors can utilise this information to obtain access to them for a variety of reasons, including financial gain, extortion, political or societal benefit, or simple devastation. As a result, it's vital to have a comprehensive cybersecurity policy in place to protect sensitive data against high-profile security breaches.
What is Palo Alto?
Palo Alto Networks, the world's leading cybersecurity company, is helping to shape the cloud-centric future with technology that is changing the way people and businesses work. Palo Alto’s objective is to be the go-to cybersecurity partner for safeguarding digital lives. With ongoing innovation that capitalises on the latest discoveries in artificial intelligence, analytics, automation, and orchestration, Palo Alto helps address the world's most pressing security concerns.

Palo Alto Networks is at the forefront of securing tens of thousands of companies spanning clouds, networks, and mobile devices by delivering a comprehensive portfolio and empowering a growing ecosystem of partners. Palo Alto users praise its stability and dependability, as well as its advanced capabilities such as application visibility, which make the learning curve worthwhile. When performance and advanced features are more important than affordability, Palo Alto is a good option.
Here, we have provided the top interview questions that can help you crack any interview process linked to Palo Alto, whether you're a fresher or an experienced professional.
Palo Alto Interview Questions for Freshers
1. Can you tell me the default IP address, as well as the default login and password, for Palo Alto Firewall's administration port?
In the Palo Alto Firewall, the administration port's default IP address is 192.168.1.1. The username is "admin," and the password is "admin."


 Real-Life Problems
Real-Life Problems
 Prep for Target Roles
Prep for Target Roles
 Custom Plan Duration
Custom Plan Duration
 Flexible Plans
Flexible Plans
2. What exactly is a wildfire? Could you give a basic description of how wildfire works?
Finding solutions and analysing malware to protect a network from potential attacks is a time-consuming procedure. Wildfire is a cloud-based malware detection service that aids in the detection of unknown files or threats created by attackers. Wildfire provides enterprises with immediate protection and danger intelligence.
The WildFire Analysis Environment detects and blocks previously unknown malware by creating signatures that Palo Alto Networks firewalls can employ to detect and stop it. When a Palo Alto Networks firewall identifies an unknown sample (a file or a link included in an email), it can send the sample to WildFire for analysis. WildFire classifies a sample as benign, grayware, phishing, or malicious based on the traits, behaviours, and activities it exhibits when examined and performed in the WildFire sandbox. WildFire then creates signatures to recognise the freshly identified malware and makes the most recent signatures available globally in real-time for retrieval. The malware originally detected by a single Palo Alto Networks firewall can subsequently be automatically blocked by all Palo Alto Networks firewalls by comparing incoming samples against these signatures. From the time where a user downloads a file containing an advanced VM-aware payload until the point where WildFire develops a signature package utilised by Palo Alto Networks firewalls to protect against future malware exposure, the following sequence explains the WildFire process lifecycle.

3. What is the maximum number of zones that an interface can be a part of?
Security zones on the firewall are a logical approach to arrange physical and virtual interfaces in order to restrict and log traffic that passes through certain network interfaces. Before an interface on the firewall can process traffic, it must be allocated to a security zone. Multiple interfaces of the same type (such as tap, layer 2, or layer 3 interfaces) can be allocated to a zone, but an interface can only belong to one zone.
4. Could you clarify the various states of the HA Firewall?
The various states of the HA firewall are:
- Initial
- Passive
- Active
- Active-primary
- Active-secondary
- Tentative
- Non-functional
- Suspended
5. How to perform policy match and connectivity tests from the web interface?
Instead of using the CLI, you can use the web interface to execute policy match and connectivity checks for firewalls in PAN-OS 9.0. You can simply validate traffic and connectivity to ensure that policy rules are matching policy rules as expected to allow or reject traffic and that firewalls can connect to network resources and external services like WildFire, Log Collectors, and the Update Server.
- Go to the firewall's web interface and log in.
- To execute a policy match or connectivity test, go to DeviceTroubleshooting.
- To run the policy match test, fill in the required information.
- Conduct out the policy matching test.
- To get the Result Details for the policy rule that matches the test criteria, click the policy rule Test Result.
 Learn via our Video Courses
Learn via our Video Courses
6. How does an APP-ID work?
App-ID is used to identify applications on your network in the following way:
- Traffic is compared to policy to see if it is authorised on the network.
- The application is then identified by applying signatures to approved traffic based on application traits and transaction characteristics that are unique to the application. The signature also determines whether or not the application is running on its default port. If the traffic is allowed by policy, it is checked for threats and studied further so that the application may be identified.
- If App-ID detects encryption (SSL or SSH) and a Decryption policy rule is in place, the session is decrypted and application signatures are applied again to the decrypted flow.
- Additional context-based signatures are applied to decoders for well-known protocols in order to detect other apps that may be tunnelling within the protocol (for example, Yahoo! Instant Messenger via HTTP). Decoders ensure that traffic follows protocol standards, and they make NAT traversal and dynamic pinhole opening easier for applications like SIP and FTP.
- Heuristics or behavioural analysis may be used to establish the identity of apps that are exceptionally evasive and cannot be identified by advanced signature and protocol analysis.
When an application is found, the policy check decides whether to block it or allow it to operate while screening for risks, inspecting for illegal file transfers and data patterns, or shaping it using QoS.
7. Is the firewall at Palo Alto stateful?
Yes, because all firewall traffic can be routed through the Palo Alto system and then matched against a session. More importantly, each session should be compared against a security policy set by the firewall.


 Real-Life Problems
Real-Life Problems
 Detailed reports
Detailed reports
8. In Palo Alto, what is the difference between virtual routers and virtual systems?
Virtual routers:
- A virtual router is a Layer 3 routing mechanism built into a firewall. The firewall can use virtual routers to gain routes to other subnets, and you can manually establish static routes or participate in one or more Layer 3 routing protocols (dynamic routes).
- You can also establish numerous virtual routers (VR), each with its own set of routes that are not shared among them, allowing you to configure various routing behaviours for distinct interfaces.
Numerous VSYS can share the same VR, and multiple VSYS can have multiple VRs.
Virtual systems:
- Virtual systems are distinct, logical firewall instances within a single physical Palo Alto Networks firewall. A virtual system is made up of physical and logical interfaces and subinterfaces, virtual routers, and security zones (including VLANs and virtual wires). Each virtual system's deployment mode (any combination of virtual wire, Layer 2, or Layer 3) is selected by you.
- Instead of having several firewalls, controlled service providers and organisations should employ a single pair of firewalls (for high availability) and allow virtual environments to run on them. Each virtual system can act as its own firewall, with its own security policy, interfaces, and administrators. This allows you to segment the management of all policies, reporting, and visibility capabilities provided by the firewall. You can logically separate physical networks by enabling virtual systems on your firewall.
9. What is the purpose of Palo Alto AutoFocus?
Palo Alto Auto Focus is a Palo Alto service that may detect major attacks and respond appropriately without the need for additional resources. The service is a cloud-based threat intelligence service.
WildFireTM, the PAN-DB URL Filtering database, Unit 42, and third-party feeds are all used by AutoFocus (including both closed and open-source intelligence). After that, AutoFocus makes the data searchable and layers it with statistics that both emphasise pervasive malware and reveal malware linkages.
Benefits:
- Get unprecedented visibility into attacks by combining data from the industry's largest network, endpoint, and cloud intelligence sources.
- Every threat will be enriched with the most detailed context from world-renowned Unit 42 threat researchers.
- With a unique threat feed and agile APIs, analysts can get a significant time advantage with intel embedded in any tool.
10. What are the different failover scenarios?
The event is known as a failover when one firewall fails and the peer takes over the role of safeguarding traffic. When a monitored metric on a firewall in the HA pair fails, for example, a failover is initiated.
The scenarios that explain the failure over triggering are as follows:
-
Hello messages and heartbeat polling:
- Hello messages and heartbeats are used by the firewalls to ensure that the peer firewall is responsive and working. To validate the state of the firewall, hello messages are delivered from one peer to the other at the configured Hello Interval.
- The heartbeat is an ICMP ping over the control link to the HA peer, to which the peer responds to confirm that the firewalls are connected and responding. The heartbeat interval is 1000 milliseconds by default. Every 1000 milliseconds, a ping is issued, and if three consecutive heartbeat losses occur, a failover happens.
-
Link monitoring:
- The monitored physical interfaces are organised into a link group, and their status (link up or link down) is tracked. One or more physical interfaces can be found in a link group. When any or all of the interfaces in a group fail, a firewall failure occurs. The default behaviour is that if any link in the link group fails, the firewall will set the HA status to non-functional (or tentative in active/active mode) to signify a monitored object failure.
-
Path monitoring:
- Path Monitoring keeps track of the whole network path to mission-critical IP addresses. Pings using the ICMP protocol are used to check if an IP address is reachable. Ping intervals are set to 200ms by default. When 10 consecutive pings (the default value) fail, an IP address is declared unreachable, and a firewall failure occurs when any or all of the monitored IP addresses become unreachable. The default behaviour is that if any of the IP addresses becomes unreachable, the firewall will set the HA state to non-functional (or tentative in active/active mode) to signify a monitored object failure.
- A failover happens when the administrator suspends the firewall or when preemption occurs, in addition to the above failover triggers.
11. In Palo Alto, what is a U-turn NAT?
In Palo Alto, the U-turn NAT is just a logical path employed in the networking system. The user should be able to access the internal DMZ servers using this NAT profile. You should utilise the external IP address of the respective servers to accomplish this.
12. Explain Active/passive and Active/Active modes in Palo Alto?
-
Active/Passive:
- One firewall manages traffic actively, while the other is synced and ready to switch to active mode if one fails. Both firewalls use identical configuration parameters in this mode, and one actively handles traffic until a path, connection, system, or network fails. When the active firewall fails, the passive firewall easily shifts to the active state and maintains network security by enforcing the same regulations. In virtual wire, Layer 2, and Layer 3 deployments, active/passive HA is supported.
-
Active/Active:
- Both firewalls in the pair are active and processing traffic, and they manage session setup and ownership in a synchronised manner. Both firewalls keep their own session and routing tables and synchronise with one another. In virtual wire and Layer 3 deployments, active/active HA is supported.
- We should consider the following distinctions when selecting whether to employ active/passive or active/active mode:
- It is substantially easier to troubleshoot routing and traffic flow issues in active/passive mode due to its simplicity of design. Layer 2 deployment is supported in active/passive mode but not in active/active mode.
- Advanced design concepts are required for active/active mode, which might result in more complicated networks. Activating networking protocols on both firewalls, duplicating NAT pools, and deploying floating IP addresses, depending on how you implement active/active HA, may necessitate additional settings. Because both firewalls are actively processing traffic, they execute Layer 7 content inspection using the notions of session owner and session setup. If each firewall requires its own routing instances and you need full, real-time redundancy from both firewalls all of the time, active/active mode is advised. Because both firewalls are actively processing traffic, active/active mode has a faster failover and can handle peak traffic flows better than active/passive mode.
13. What is a zone protection profile?
The Zone protection profile will provide you with total protection against attacks such as floods, reconnaissance, and packet-based attacks. Flood attacks can be of several types, including SYN, ICMP, and UDP. You'll be able to guard against port and host sweeps using the reconnaissance protections. The packet safeguards assist you in defending against big ICMP and ICMP fragment attacks.
It is intended to provide broad-based security at the ingress zone (the zone where traffic enters the firewall), rather than protecting a specific end host or traffic heading to a specific destination zone. A zone can have just one zone protection profile attached to it. Configure a DoS Protection policy (Policies > DoS Protection) to match on a specific zone, interface, IP address, or user to enhance zone protection capabilities on the firewall.
Because zone protection is based on new connections per second (cps), not packets per second, it is only implemented when there is no session match for the packet (pps). The zone protection option will be bypassed if the packet matches an existing session.
14. What is the Application Command Centre (ACC)?
The Application Command Centre (ACC) provides an interactive graphical summary of the applications, users, URLs, threats, and information traversing your network. The firewall logs are used by the ACC to provide visibility into traffic patterns and actionable threat information. The ACC interface offers a tabbed view of network activity, threat activity, and blocked activity, with relevant widgets on each tab for better network traffic visualisation. The graphical representation enables you to engage with the data and visualise the connections between network events, allowing you to spot abnormalities and improve your network security rules. You can also add a custom tab and include widgets that allow you to drill down into the information that is most important to you for a more personalised picture of your network.
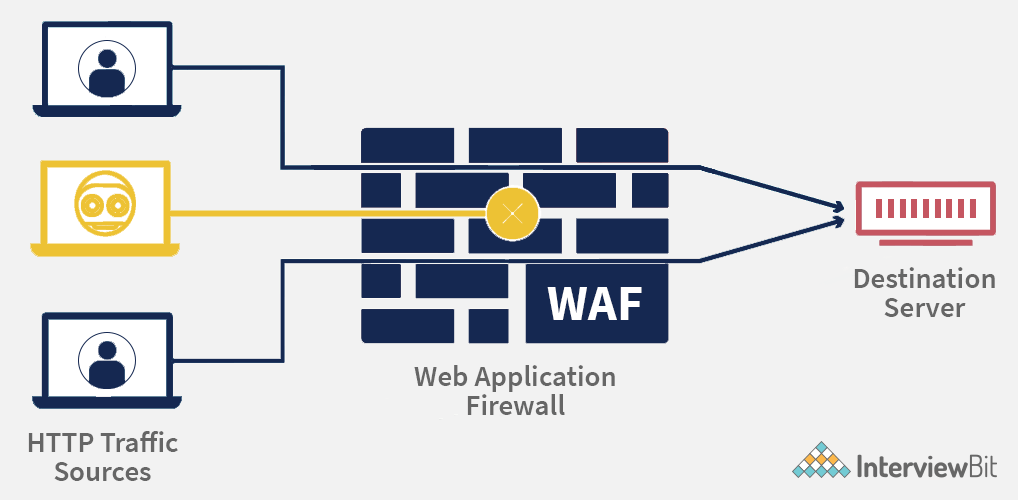
15. What is WAF (Web Application Firewall)?
The Web Application Firewall (WAF) is the acronym for Web Application Firewall. WAF's main purpose is to keep track of web applications and improve their security and functionality. It protects the web application by filtering traffic between the internet and the application.
Web Application Firewalls include the following key features:
- Designed to compensate for insecure coding techniques - only enterprises who employ web apps and are concerned about the security of their code should purchase a WAF.
- Highly customised for each environment — examining how the web application should behave and intervening if it does not.
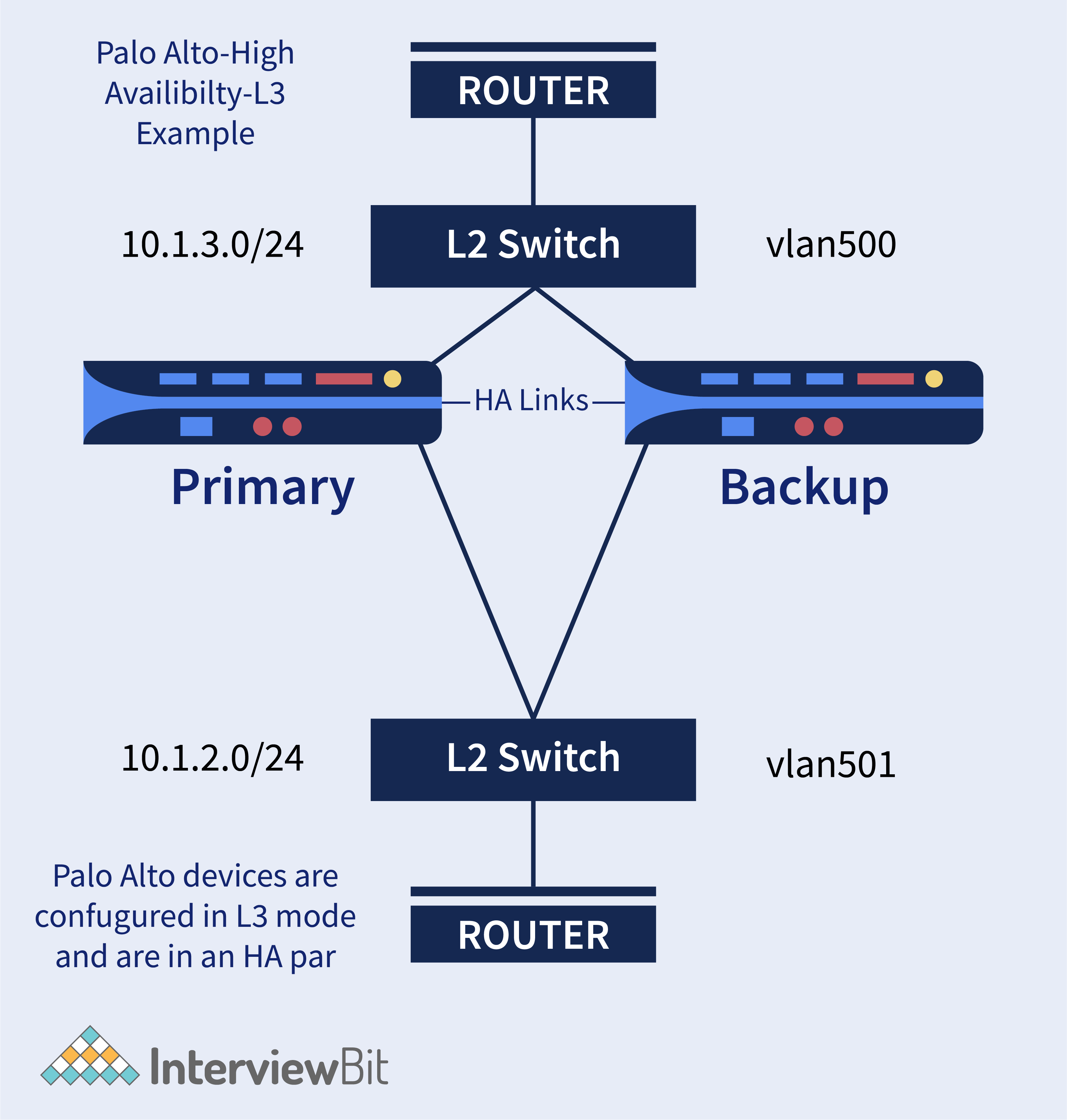
16. In Palo Alto, what do HA, HA1, and HA2 mean?
- HA stands for High Availability, which is a Palo Alto deployment model. HA is used in a network to prevent a single point of failure. It includes two firewalls that are set up in a synchronised fashion. Security features are enforced through a different firewall if one fails. The company will be able to continue operating without interruption as a result of this.
- There are two different ports in HA: HA1 and HA2. HA1 is referred to as a control link, while HA 2 is referred to as a datalink. These ports are used to synchronise data and keep track of the current state.
- Hellos, heartbeats, and HA state information are exchanged across the HA1 link, as well as management plane sync for routing and User-ID information. This connection is often used by firewalls to synchronise configuration updates with their peers. The HA1 link is a Layer 3 link that necessitates the use of an IP address.
- Between firewalls in a HA pair, the HA2 link is used to synchronise sessions, forwarding tables, IPSec security associations, and ARP tables. Except for the HA2 keep-alive, data flow on the HA2 connection is always unidirectional; it flows from the active or active-primary firewall to the passive or active-secondary firewall. The HA2 link is a Layer 2 link that defaults to ether type 0x7261.
17. What is Palo Alto's architectural style?
Palo Alto Networks' next-generation firewalls are built on single-pass parallel processing (SP3) architecture that provides high-throughput, low-latency network protection while also including cutting-edge features and technologies.
Palo Alto Networks' SP3 architecture, which combines two complementing components, tackles the performance concerns that afflict today's security infrastructure. The components are:
- Single Pass software.
- Parallel Processing hardware.
As a result, today's high-performance networks have the ideal blend of raw throughput, transaction processing, and network security.
18. What exactly is an APP-ID?
App-ID is the abbreviated name for application identifications. This is one of Palo Alto's most important elements. App-ID's primary tasks include recognising apps and traversing firewalls independently.
App-ID allows you to see and learn about the applications on your network, including how they work, their behavioural features, and their risk level. App-ID, a patented traffic classification technology exclusive to Palo Alto Networks firewalls, determines what an application is regardless of its port, protocol, encryption (SSH or SSL), or any other invasive approach. To effectively identify apps, it uses a combination of classification mechanisms—application signatures, application protocol decoding, and heuristics—on your network traffic stream. This enables for more precise management, such as permitting just sanctioned Office 365 accounts or allowing Slack for instant messaging but not file transmission.
19. In Palo Alto, identify the various deployment modes. ?
There are four deployment models to choose from:
- Tap mode deployment option
- Virtual (V-Wire) Deployment option
- Layer 2 deployment option
- Layer 3 deployment option
1. Tap mode deployment option:
With the use of a tap or switch SPAN/mirror port, users can observe any form of traffic flow throughout the networking system. This deployment option has the advantage of allowing enterprises to closely monitor traffic to their servers or networks without requiring any network infrastructure upgrades.
It's critical to configure the correct SPAN source and SPAN destination ports, as well as enable Tap mode on the Firewall while configuring SPAN. Although tap mode provides visibility of the application, user, and content, we must keep in mind that the firewall is unable to manage traffic in this mode because no security rules can be enforced. Tap mode just adds visibility to the dashboard's ACC tab. The catch is that the tap interface needs to be allocated to a security zone.
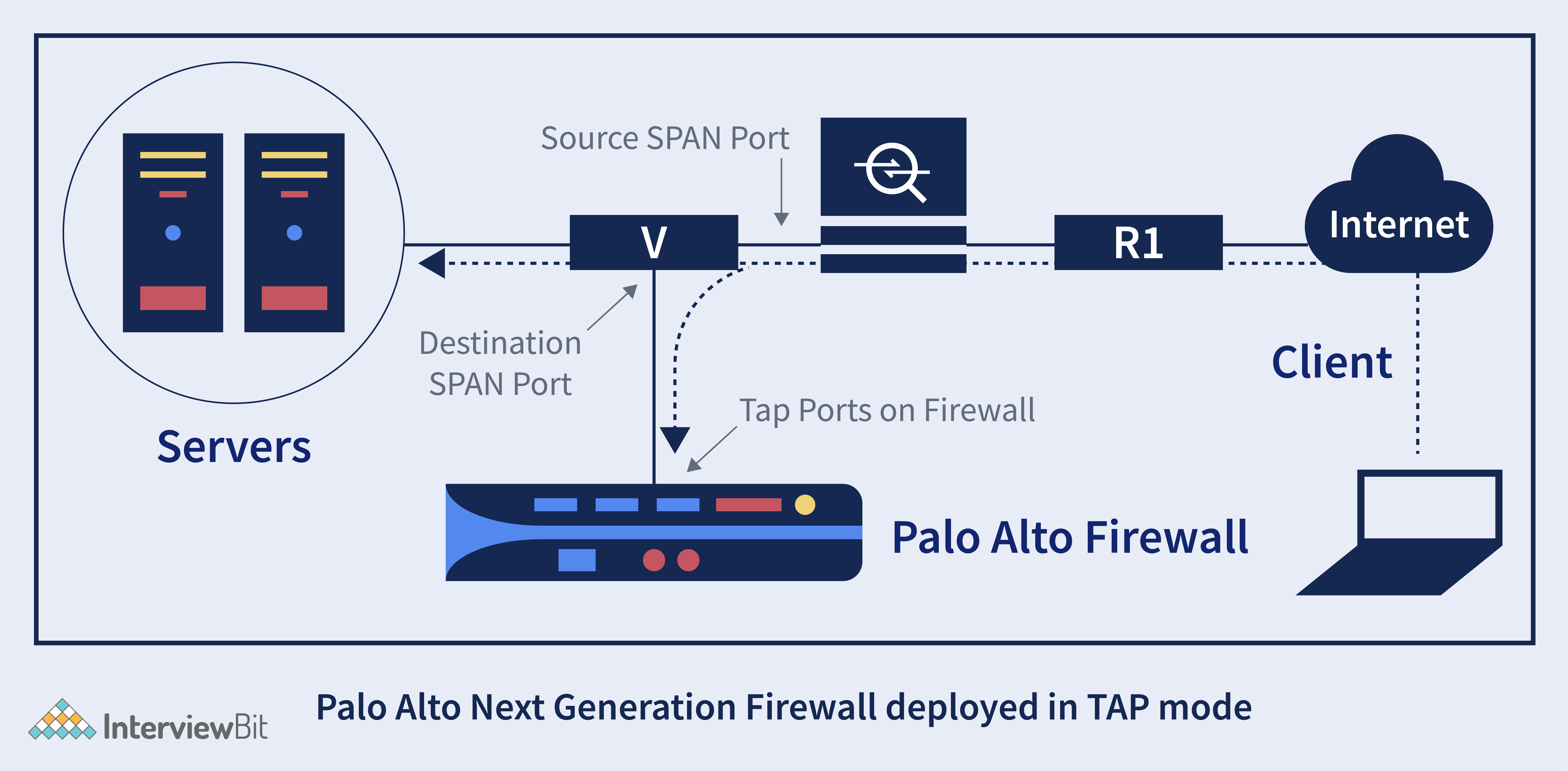
2. Virtual (V-Wire) Deployment option:
The firewall system is installed passively on any network segment using this deployment model, which combines two interfaces. Engineers can monitor and control traffic across the link with V-Wire deployment choices, which overcomes the restrictions of TAP mode deployment. App-ID, User-ID, Content-ID, NAT, and decryption are all supported via the Virtual Wire interface.
3. Layer 2 deployment option:
Multiple networking interfaces will be configured into a "virtual-switch" or VLAN mode in Layer 2 mode. The firewall is set in Layer 2 deployment mode to switch between two or more network segments. Traffic passing via the firewall is analyzed according to policies, enhancing security and visibility within the internal network.
The firewall interfaces can support Access or Trunk Links (802.1Q trunking) in this mode, but they are not part of the Spanning Tree topology. Any BPDUs received on the firewall interfaces are routed without being processed to the adjoining Layer 2 switch. A default Gateway, which is commonly a Layer 3 switch that supports InterVLAN routing, a Firewall security appliance, or even a Router-on-a-Stick design, can route traffic across VLAN networks or other networks.
4. Layer 3 deployment option:
The Palo Alto firewall routes allow traffic to flow between various interfaces in this layer 3 deployments. The IP address should be added to each interface by the user.
Layer 3 deployment mode is a common configuration. The firewall directs traffic between many interfaces in this mode, each of which has its own IP address and security zone. The Firewall interfaces can also be set up to get an IP address from a DHCP server and be used to manage the security appliance.
The diagram above depicts a typical Layer 3 deployment scenario in which the Firewall routes and regulates traffic between three IP networks. All traffic passing through the Firewall is reviewed and allowed or prohibited according to the security policies established, just like in previous setup methods.
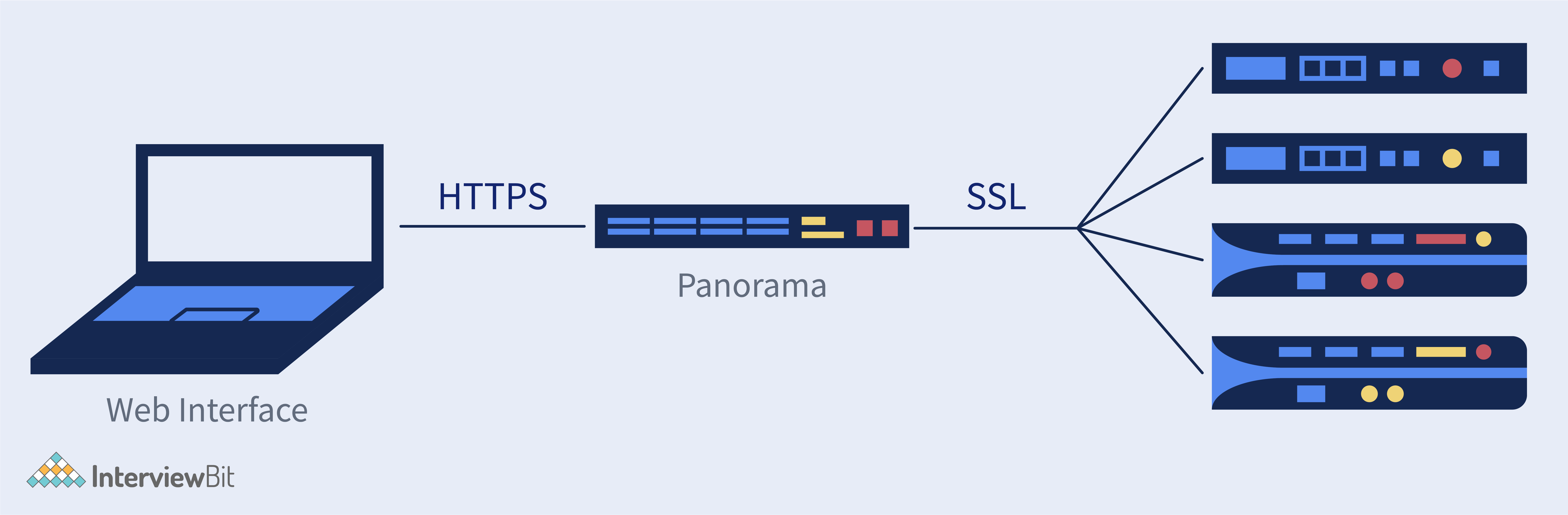
20. What arethe advantages of Panorama in Palo Alto?
The following are a few of Palo Alto's panorama benefits:
- Distributed administrations are available, allowing you to control and delegate evaluation of Palo Alto firewall configurations.
- Deployment and a centralised configuration system are provided.
- Supports logging or aggregated management for reporting and analysis with central oversight.
- View a graphical representation of the network's apps, their users, and the security implications.
- Analyze, evaluate, and report on network traffic, security issues, and administrative changes from a centralised location.
21. What are the possibilities for forwarding logs messages on the Palo Alto Firewall?
The following log forwarding options are supported by Palo Alto Networks firewalls and Panorama. Consider the logging capacity of your Panorama Models and Determine Panorama Log Storage Requirements before selecting an option.
- Logs from firewalls are forwarded to Panorama, while logs from Panorama are forwarded to external services: This option is ideal for installations where the bandwidth between firewalls and external services is insufficient to support the logging rate, which is common when the connections are remote. By offloading some processing to Panorama, this setup increases firewall performance.
- Panorama and external services receive logs from firewalls at the same time: Panorama and the external services are both endpoints of distinct log forwarding flows in this arrangement; the firewalls do not rely on Panorama to pass logs to external services. This setting is suitable for installations where the connections between firewalls and external services have enough bandwidth to support the logging rate, which is common when the connections are local.
22. What is the procedure for adding a licence to the Palo Alto Firewall?
You must first activate the licences for each of the services you purchased before you can begin utilising your firewall to safeguard network traffic.
- Locate the licence activation codes that you purchased.
- Palo Alto Networks customer care should have sent you an email with the activation codes associated with each subscription when you purchased them. If you can't find this email, you'll need to contact Customer Support to get your activation codes before continuing.
- You have to activate your Support subscription. If you don't have a valid Support licence, you won't be able to upgrade your PAN-OS software.
- Select DeviceSupport after logging in to the web portal.
- Select Activate support with authorisation code from the drop-down menu.
- Click OK after entering your Authorization Code.
- Activate each licence you've bought. Choose Device>Licences, then activate your licences and subscriptions using one of the methods below:
- License keys can be obtained via the licence server.
- Use the authorisation code to activate the functionality.
- Upload the licence key manually.
- Check to see if the licence has been activated.
- Verify that the licence has been successfully activated on the Device>Licences page. After activating the WildFire licence, for example, you should see that it is valid:
- (For WildFire subscriptions only) To complete the WildFire subscription activation, do a commit.
- A commit is required for the firewall to begin passing advanced file types after establishing a WildFire subscription.
23. What is GlobalProtect in Palo Alto?
GlobalProtectTM is an application that runs on your endpoint (desktop computer, laptop, tablet, or smartphone) to safeguard you by employing the same security standards that protect important corporate network resources. GlobalProtectTM encrypts your intranet traffic and allows you to connect to your corporate network from anywhere in the world to use your company's resources.
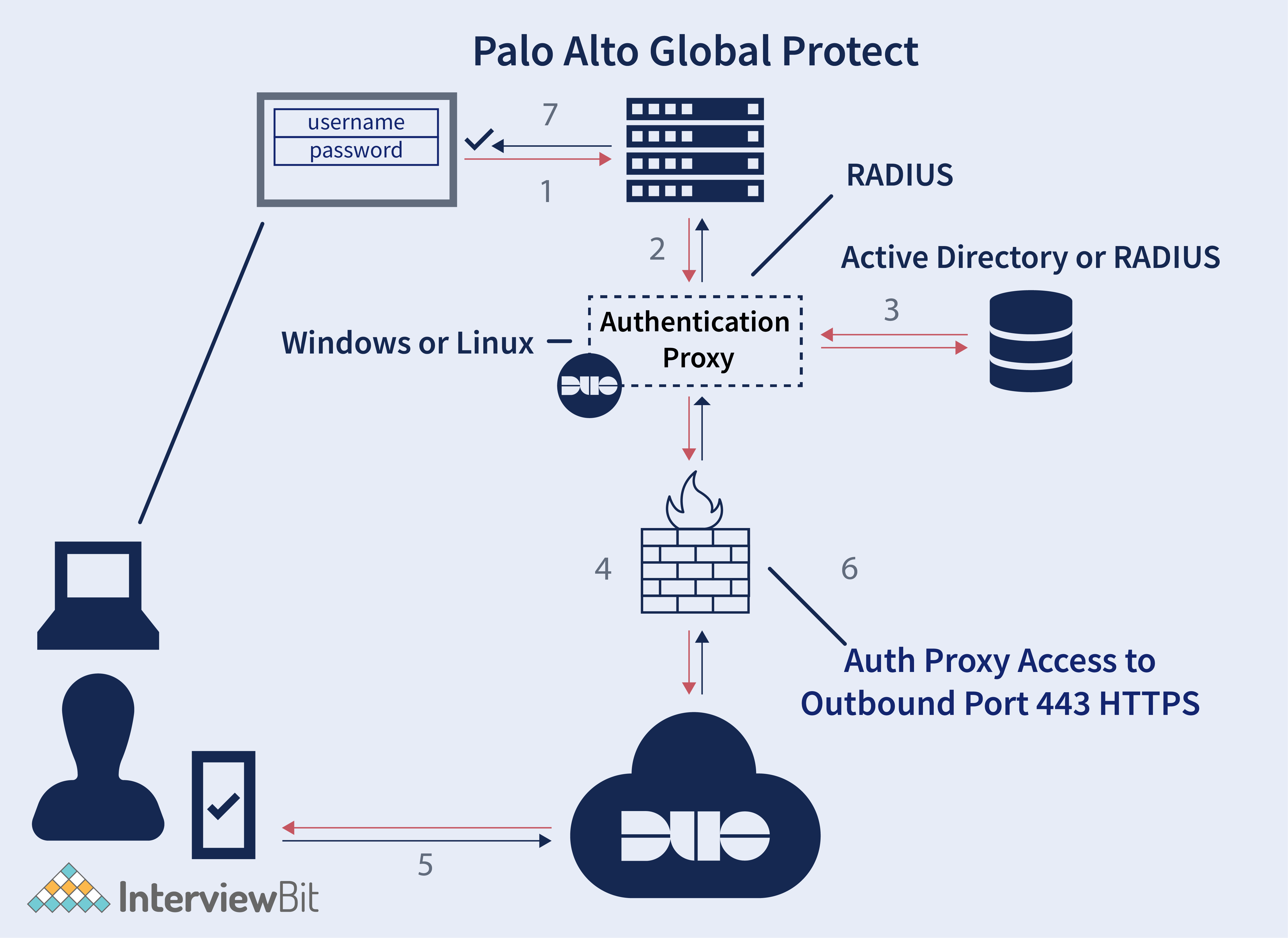
24. In Palo Alto, what do you mean by endpoint security?
Endpoints are frequently targeted in cybercrime, cyberespionage, and cyber warfare attacks. Endpoint security protects endpoints from malicious software. Computing equipment connected to a local or wide area network is referred to as an endpoint. Desktop PCs, laptops, smartphones, servers, and even Internet-of-things (IoT) devices are examples of endpoints.
Endpoint security solutions safeguard endpoints from cyber threats and unauthorised activities. Endpoint security solutions have progressed from standard antivirus to include a comprehensive set of defences to protect against known and undiscovered malware, fileless attacks, exploits, and post-intrusion attack tactics. Endpoint security solutions are frequently able to isolate compromised endpoints, preventing assaults from spreading to numerous endpoints, because threat actors may target endpoints as a conduit into an organisation's network.
25. Mention the various types of linkages used to establish HA or the HA introduction?
To establish HA or HA introduction, there are four sorts of linkages:
- HA1 or control link
- HA2 or Datalink
- Back-up links
- Packet forwarding links
26. What are Backup Links?
Back-up links ensure that the HA1 and HA2 links are redundant. When dedicated backup links are not available, in-band ports can be used for backup links for both HA1 and HA2 connections. When configuring backup HA links, keep the following in mind:
- The primary and backup HA links' IP addresses must not be in the same range.
- Backup HA links must be on a separate subnet than primary HA links.
- On distinct physical ports, HA1-backup and HA2-backup ports must be configured. Ports 28770 and 28260 are used by the HA1-backup link.
- For the HA1-backup link, PA-3200 Series firewalls do not support IPv6; instead, use an IPv4 address.
27. Mention the various port numbers used in HA?
The different port numbers that are used in HA are:
The HA1 control link uses TCP 28769 and TCP 28260 for text communication that is clear between the HA peer firewalls. The HA1 link is a Layer 3 link that necessitates the use of an IP address.
The HA1 control link uses TCP 28 to communicate securely (SSH over TCP) between HA peer firewalls.
For HA1 backup links, use TCP 28770 as a listening port.
TCP 28771 is used to backup heartbeats. If you use an in-band port for the HA1 or HA1 backup connections, Palo Alto Networks advises setting heartbeat backup on the MGT interface.
IP 99 and UDP 29281 synchronises sessions, forwarding tables, IPSec security associations, and ARP tables between firewalls in a HA pair via the HA2 link. The HA2 link's data flow is constantly constant. Data flows unidirectionally from the active firewall (Active/Passive) or active-primary (Active/Active) to the passive firewall (Active/Passive) or active-secondary (Active/Active) on the HA2 link (save for the HA2 keep-alive). The HA2 link is a Layer 2 link that defaults to ether type 0x7261.
The HA data connection can also be configured to use IP (protocol number 99) or UDP (port 29281) as the transport, allowing it to cross subnets.
28. What functionalities does Palo Alto support when it's in virtual wire mode?
In virtual wire mode, Palo Alto supports a number of features, including App-ID, Decryption, Content-ID, User-ID, and NAT.
29. Can you tell me which virtualization platform fully supports Palo Alto network deployments?
The Palo Alto Networks VM-Series virtualization platform aids Palo Alto Networks deployment significantly. It offers open stack, VMware, Cisco ACI, Amazon Web Services, Google Cloud Platform, and others as public and private cloud computing environments.
30. Can you find out which command is used to show the maximum size of the log file? Give a quick overview of how Panorama handles new logs once the storage limit has been reached.
The following is the command that is used to see the maximum log file size: show logdb-quota on the system
Panorama automatically deletes old logs and makes room for new records when the log storage limit is reached. The panorama includes an automated feature that can assess the storage limit and, if necessary, eliminate it.
Palo Alto Interview Questions for Experienced
1. How do Palo Alto NGFW and WAF differ?
Palo Alto Networks' next-generation firewalls leverage three distinct identification technologies: App-ID, User-ID, and Content-ID, to provide policy-based visibility and control over apps, users, and content. Knowing which applications are traversing the network and who is using them allows firewall security policies to be created, such as access control, SSL decryption, threat detection, prevention, and URL filtering. Every company requires a firewall.
A Web Application Firewall(WAF), on the other hand, is meant to look at web apps and monitor them for security concerns that may occur as a result of various coding errors The only thing the two methods have in common is that they both use the name firewall. A WAF is only required for companies who believe their web apps have coding issues.
2. Give a detailed explanation of the Tentative HA Firewall state.
One of the following causes the state of a firewall (in an active/active configuration):
- When a firewall has failed.
- A monitored object's failure (a link or path).
- When the firewall goes into a suspended or non-working condition.
Sessions and configurations from the peer are synchronised via a firewall in a provisional state.
- When a firewall in a virtual wire deployment enters a tentative state owing to a path failure and gets a packet to forward, it passes the packet to the peer firewall for processing through the HA3 connection. The packet is processed by the peer firewall and transmitted back to the firewall through the HA3 link to be sent out the egress interface. In a virtual wire deployment, this behaviour keeps the forwarding path intact.
- When a firewall in the tentative state receives a packet in a Layer 3 deployment, it transmits it over the HA3 connection to the peer firewall to own or set up the session. This firewall either sends the packet out to the destination or sends it back to the peer in a tentative state for forwarding, depending on the network topology.
The Tentative Hold Time is activated and routing convergence happens after the failed path or link clears or when a failed firewall changes from tentative to active-secondary state. Before processing any packets, the firewall tries to establish routing adjacencies and populate its route table. Without this timer, the recovering firewall would quickly enter active-secondary mode and silently discard packets due to a lack of sufficient routes.
After links are up and able to receive incoming packets, a firewall exits suspended mode and enters tentative mode for the Tentative Hold Time. Tentative Hold Time range (sec) can be disabled (default is 0 seconds) or set to a value between 10 and 600 seconds; the default is 60.
3. What are the steps to take configuration Backup of the Palo alto firewall?
Backup of Palo Alto Firewall Configuration:
- After logging into the Palo Alto firewall, go to Device -> Setup -> Operations.
- To save the settings locally to the Palo Alto firewall, click "Save named configuration snapshot."
- To save a backup of the Palo Alto Configuration file to your local PC, click "Export Named Configuration Snapshot."
4. What determines whether a primary and secondary HA pair exists?
The parameter "Device ID" determines this. Set the Device ID in an active/active setting to identify which peer will be active-primary (set Device ID to 0) and which will be active-secondary (set Device ID to 1). (set the Device ID to 1).
5. What do you understand about dynamic updates?
Palo Alto Networks publishes updates about new and modified apps, threat protection, and Global Protect data files on a regular basis via dynamic updates. You can determine the frequency at which the firewall checks for and downloads or install new updates by creating a schedule for dynamic updates. You can set the frequency of updates retrieval using the "schedule" option. You can choose whether to "Download Only" or "Download and Install" scheduled updates, as well as how often and when they occur (the "Recurrence" and time).
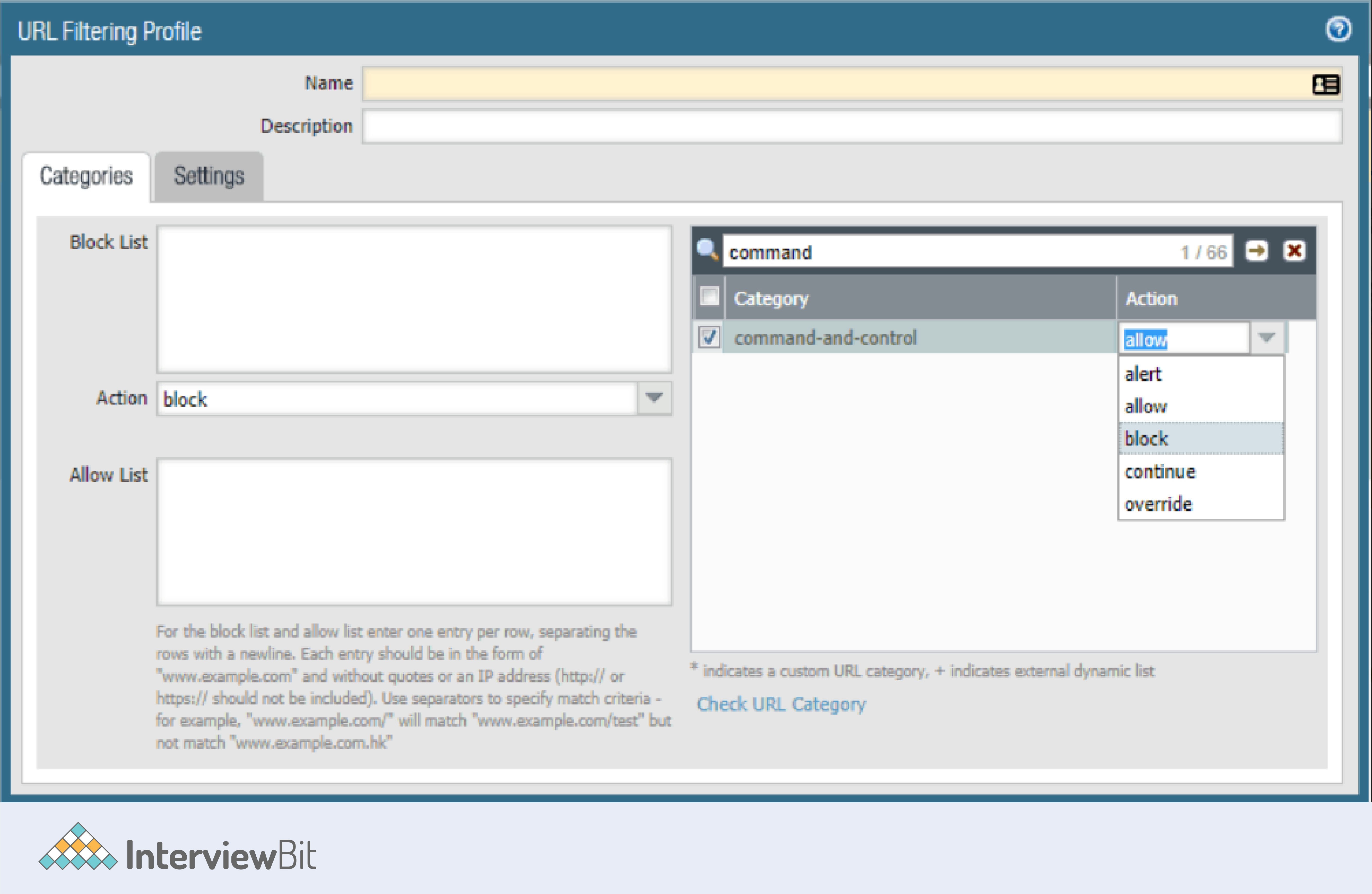
6. What options are there for filtering URLs?
The actions accessible while filtering URLs are as follows.
- Alert: The website is allowed, and a log entry is created in the URL filtering log. To log and see what's going on, set an alert as the Action for categories of traffic that you don't wish to restrict.
- Allow: The website is allowed to be visited, and no log entries are kept.
- Block: The user will see a response page and will be unable to proceed if the website is restricted. An entry is created in the URL filtering log.
- Continue: The user will be sent to a response page advising them that the site has been blocked due to company policy, but that they can still view it. When you prohibit site access for a URL category, you also block User Credential Submissions for that category. The continue action is often used for benign categories, and it is designed to improve the user experience by allowing them to continue if they believe the site is erroneously classified. The message on the response page can be customised to include information particular to your business. In the URL filtering log, an item is created.
- Override: Override: A response page will appear, notifying the user that access to websites in the specified category requires a password. With this option, the security admin or helpdesk person would provide a password that would grant temporary access to all websites in the chosen category. A record is created in the URL filtering log.
- None: Only custom URL categories are affected by the none action. If there are multiple URL profiles, select none to ensure that the custom category has no effect on the other profiles. If you have two URL profiles and the custom URL category is set to block in one, you must set the action to none in the other to prevent the block action from being applied to the second profile. A custom URL category must also be set to none in any profile where it is used in order to be deleted.
7. What are the prerequisites for Active/Passive HA?
You'll need a pair of Palo Alto Networks firewalls that match the following requirements to set up high availability:
- Both firewalls in the pair must be of the same model, whether in terms of hardware or virtualization.
- Both firewalls should be running the same version of PAN-OS, and the application, URL, and threat databases should all be updated.
- On both firewalls, the same multi virtual system capability must be activated or disabled. When a firewall is enabled, it necessitates the purchase of an additional virtual system licence.
- Dedicated HA links or a mix of the management port and in-band ports configured as HA interfaces—the same interfaces.
- Determine the IP address for the HA1 (control) connection between the HA peers. Both peers' HA1 IP addresses must be on the same subnet if they are directly connected or connected to the same switch. The control connection can be made using the management port on firewalls without specific HA ports. Using the management port creates a direct link between both firewalls' management planes. Because the management ports will not be directly connected between the peers, make sure you have a route that connects the two interfaces across your network.
If you're utilising Layer 3 as the transport mechanism, find the IP address for the HA2 (data) connection. Choose Layer 3 if the HA2 link must communicate over a routed network. The HA2 connections' IP subnet must not be the same as the HA1 links' IP subnet or any other subnet assigned to the firewall's data ports. - The same set of licences— Each firewall's licences are unique and cannot be shared. As a result, both firewalls must be licensed in the same way. If neither firewall has the same set of licences, they will be unable to synchronise configuration information and preserve parity for a seamless failover.
8. On Palo Alto NGFWs, what types of logs can be viewed?
All logs are shown by the firewall, ensuring that role-based administration rights are respected. Only the information that you are allowed to see is available, which varies based on the logs you're looking at. You can view Traffic Logs, Threat Logs, URL Filtering Logs, WildFire Submissions Logs, Data Filtering Logs, HIP Match logs, GTP logs, Tunnel Inspection Logs, Unified logs, SCTP logs, System logs, Alarm logs, Authentication logs and Configuration logs, etc.
9. Explain Unified log type.
In a single view, the most recent log entries for Traffic, Threat, URL Filtering, WildFire Submissions, and Data Filtering are displayed. The collective log view allows you to look into and filter these many types of logs all at once (instead of searching each log set separately). Alternatively, you can select which log kinds to view by clicking the arrow to the left of the filter field and selecting traffic, threat, url, data, and/or wildfire.
10. What is the role of the Virtual Wire interface in the Palo Alto firewall?
A virtual wire connects two Ethernet interfaces logically, allowing all traffic or only traffic with certain VLAN tags to pass between them (no other switching or routing services are available). To classify communication based on an IP address, IP range, or subnet, virtual wire subinterfaces can be created. A virtual wire does not necessitate any adjustments to adjacent network devices. A virtual wire can connect two Ethernet interfaces that are on the same medium (copper or fibre optic), or connect a copper interface to a fibre optic interface.
Decide which two interfaces to bind (NetworkInterfacesEthernet) and configure their settings accordingly to create a virtual wire.

11. A Network Security Engineer in an Enterprise Deployment wants to assign to a group of administrators without having to create local administrator accounts on the firewall. Which method of authentication must be used?
RADIUS with Vendor-Specific Attributes must be used.
12. Could you perhaps clarify why Palo Alto is regarded as a next-generation firewall?
The Palo Alto cybersecurity application contains all of the necessary features for the next generation. An infusion prevention system and control functions are included in this application. It is believed to be different from other cybersecurity suppliers in terms of productivity. One of the most important aspects is that it uses a single platform to deliver next-generation features.
With sophisticated traffic identification, malware prevention, and threat intelligence technologies, Palo Alto Networks Next-Generation Firewalls (NGFW) allow security teams comprehensive visibility and control over all network traffic. Palo Alto NGFWs give enterprises a variety of advanced security tools and techniques to intelligently decide which apps, users, and information traversing the network are safe—and which are not—rather than relying on port and protocol to safeguard network traffic from malicious attacks.
The following services are provided by Palo Alto Next-Generation Firewall:
-
Secure Application Enablement:
- App-ID: App-ID is a firewall capability from Palo Alto Networks that analyses network traffic using up to four different traffic classification algorithms to determine the identity of any application traffic on the network.
- User-ID: The User-ID functionality, which is included with all Palo Alto Networks firewalls, allows enterprises to track user activity using user- or group-based enablement policies rather than IP addresses alone.
- Content-ID: Content-ID can securely enable approved applications by prohibiting vulnerability exploits, malware, viruses, and other dangers from spreading on the network—regardless of port or encryption—after App-ID has blocked unauthorised and/or dangerous programmes. In addition to data filtering and online browsing controls, Content-ID includes a URL database.
-
Malware Detection and Prevention:
- Threat Prevention Service - Integrating with Palo Alto Networks NGFWs, the Threat Prevention service provides an extra layer of intrusion detection and prevention capabilities to protect enterprises' vital assets.
- WildFire - WildFire is a cloud-delivered malware prevention service that detects extremely advanced and previously undiscovered threats across the company using machine learning and multiple analysis methodologies.
-
DNS Security:
- The DNS Security service, which is available on all Palo Alto Networks NGFWs, provides further network security against DNS-based attacks, including advanced DNS tunnelling threats. Any DNS-based attacks discovered are automatically identified and sinkholed, allowing the security team to immediately neutralise the threat with little or no manual input.
-
Panorama Security Management:
- Panorama is a security management platform for Palo Alto Networks NGFWs that allows security teams to view firewall traffic, manage firewall configurations, expedite security automation, and handle a range of other essential security activities from a single, centralised control panel.
-
Threat Intelligence:
- AutoFocus - AutoFocus is a worldwide threat intelligence solution that complements Palo Alto Networks NGFWs' threat protection and analysis efforts. AutoFocus assists companies in detecting previously undisclosed high-impact risks and providing the threat intelligence and context required to properly mitigate the danger.
13. Explain Single Pass Software and Parallel Processing Hardware.
Single Pass Software:
Within the Palo Alto Networks next-generation firewall, the Palo Alto Networks Single Pass software is meant to achieve two critical purposes. The single-pass software, for starters, only conducts operations once per packet. Networking functions, policy lookup, application identification and decoding, and signature matching for all threats and content are all executed once when a packet is processed. The amount of processing overhead required to conduct numerous functions in a single security device is greatly reduced as a result of this. Second, Palo Alto Networks' Single Pass software's content scanning step is stream-based and uses uniform signature matching to detect and prevent threats.
With all security mechanisms engaged, our Single Pass traffic processing offers exceptionally fast throughput and minimal latency. It also comes with a single, fully integrated policy that simplifies and simplifies enterprise network security management.
Parallel Processing Hardware:
Hardware is the important component of Palo Alto Networks SP3 Architecture. Parallel Processing hardware is used in Palo Alto Networks' next-generation firewalls to ensure that the Single Pass software operates quickly. Palo Alto Networks developers first created data and control planes that were independent. Due to the separation of data and control planes, the strong utilisation of one will not negatively influence the other. For example, an administrator may be running an extremely processor-intensive report while processing packets would be fully unaffected.
The employment of discrete, specialised processing groups that work in harmony to accomplish numerous vital operations is the second important aspect of the Parallel Processing hardware.
- Routing, flow lookup, statistics counting, NAT, and other network-specific activities are all executed on network-specific hardware.
- A multi-core security engine with hardware acceleration for encryption, decryption, and decompression handles User-ID, App-ID, and policy.
- The content-ID content analysis employs a unique, dedicated content scanning engine.
- Without touching the data processing hardware, a dedicated management processor (with dedicated disc and RAM) handles configuration management, logging, and reporting on the controlplane.
14. In Palo Alto, what does the name HALite mean?
We need to understand PA 200 before we can define HALite. The PA-200 is a firewall that protects the network against a variety of cyberattacks. On the PA-200, there is a feature called HALite.
The PA-200 firewall supports HA lite, which is a variant of active/passive HA without session synchronisation. Configuration synchronisation and synchronisation of a few runtime items are included in HA light. When configured in Layer 3 mode, it additionally supports IPSec tunnel failover (sessions must be re-established), DHCP server lease information, DHCP client lease information, PPPoE lease information, and the firewall's forwarding table.
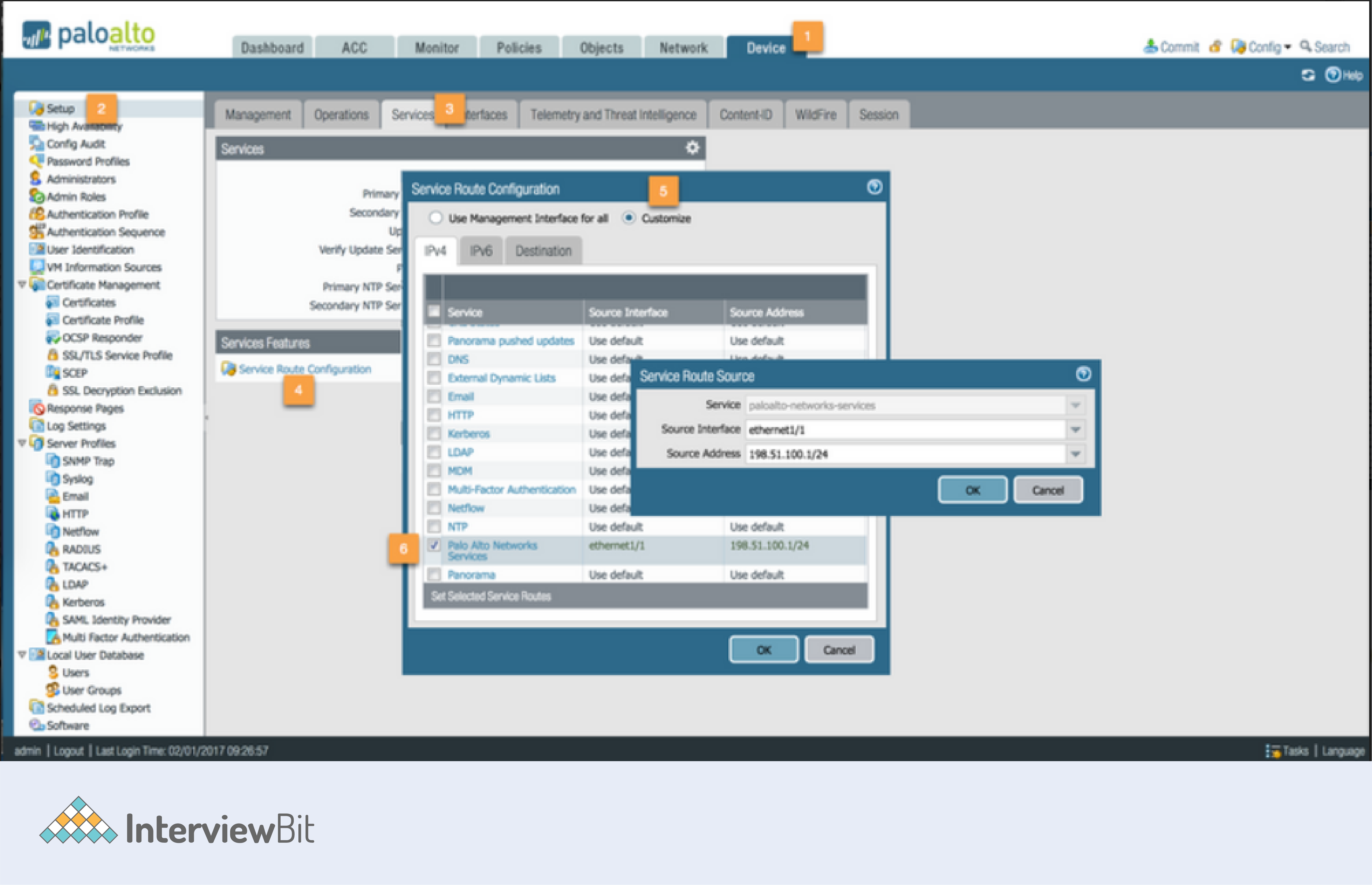
15. Define what the term "service route" means. Can you tell me which interface is used by default to access external services?
The path from the interface to the server's service is referred to as the service route. The management (MGT) interface is the default interface for accessing external sources.
16. Could you describe the basic methods for deploying certificates for Palo Alto Network Firewalls?
The basic methods for deploying certificates for Palo Alto Network Firewalls are:
- Obtain certificates from a reputable third-party certificate authority (CA): Because many browsers include root CA certificates from well-known CAs in their trusted root certificate stores, getting a certificate from a trusted third-party certificate authority (CA) like VeriSign or GoDaddy has the advantage of end clients already trusting the certificate.
- Obtain certificates from an enterprise CA: Enterprises with their own internal CA can utilise it to create and import certificates for firewall applications.
- Create a Self-Signed Root CA Certificate: You can create a Self-Signed Root CA Certificate on the firewall and use it to automatically issue certificates for other firewall apps by creating a Self-Signed Root CA Certificate.
17. What are the different types of VPN deployments that use a GlobalProtect agent?
In a Remote User-to-Site VPN implementation, the GlobalProtect agent is deployed. It's used to allow a remote user to connect to the firewall in a secure manner.
18. What sorts of media does the firewall support?
Copper and fibre optic media are supported by the Palo Alto Networks firewall.
19. In Palo Alto, which port types are recommended for use in a HA pair?
We recommend using the dedicated HA ports for HA Links and Backup Links when connecting two Palo Alto Networks® firewalls in a high availability (HA) configuration. The HA1 ports labelled HA1, HA1-A, and HA1-B are used for HA control and synchronisation traffic, whereas the HA2 and High-Speed Chassis Interconnect (HSCI) ports are utilised for HA session setup traffic. AUX-1 and AUX-2 are multipurpose auxiliary ports on the PA-5200 Series firewalls that can be configured for HA1 traffic.
The HSCI port, which is utilised for packet forwarding to the partner firewall during session setup and asymmetric traffic flow (active/active HA only), can also be configured for HA3. The HSCI port can be utilised for both HA2 and HA3 traffic.
You can use data ports as HA interfaces if your firewall doesn't have specialised HA ports. You can configure data ports as backups to dedicated HA ports if your firewall has dedicated HA ports but not a dedicated HA backup port.
20. What are the test commands we can use to verify that policies are working properly or not?
Test commands can be used to ensure that your policies are working properly.
- Test a security policy rule: To check if a security policy rule is configured correctly, use the test security-policy-match command.
- Test an Authentication policy rule: To test your Authentication policy, use the test authentication-policy-match command.
- Test a Decryption policy rule: To see if traffic to a certain destination and URL category will be decrypted according to your policy rules, use the test decryption-policy-match category command.
Useful Additional Resources:
Multiple Choice Questions
Firewall configuration files can be ___.
On a firewall, the management network port can be configured as to which type of interface?
Through decryption policies, a Palo Alto Networks firewall can decrypt which two types of encryptions?
Which firewall plane has a distinct processor for configuration, logging, and reporting?
Which of the following claims about App-ID content changes is correct?
Which of the following options displays the attributes that can be selected when creating application filters?
Which of the following statements about User-ID is false?
Which two components in a URL filtering security profile can have actions assigned to them?
Which types of attacks can a DoS Protection profile protect nodes from?
With a Palo Alto Networks firewall, how many zones can an interface be assigned?












 Download PDF
Download PDF



















